Equip Your Brand with LinkDaddy Cloud Services Press Release Know-how
Equip Your Brand with LinkDaddy Cloud Services Press Release Know-how
Blog Article
Enhance Information Safety With Trusted Cloud Providers
In today's interconnected electronic landscape, the importance of boosting data safety and security with trusted cloud services can not be overemphasized. As organizations browse the intricacies of protecting delicate information, the dependence on safe cloud services becomes a critical approach. By handing over data to credible cloud companies outfitted with advanced safety actions, organizations can fortify their defenses versus cyber hazards and guarantee data discretion. However, the inquiry remains: How can organizations successfully browse the myriad of options available and select a trusted cloud company that straightens with their security demands?
Importance of Data Security
Making certain durable data security steps is vital in today's digital landscape to safeguard delicate info from unauthorized accessibility and cyber dangers. With the exponential growth of data generation and storage space, companies face increasing obstacles in safeguarding their important assets. Information breaches not just lead to monetary losses but additionally damage a company's reputation and erode customer count on.

In the current period of remote job and cloud computer, the relevance of data safety and security is further amplified. Cloud services provide adaptability, cost-efficiency, and scalability, yet without appropriate safety and security steps, they can position considerable risks. Therefore, organizations must focus on information safety and security when embracing cloud solutions to avoid data breaches and maintain the stability of their procedures.
Benefits of Trusted Cloud Services
Offered the increasing significance of information safety in the digital landscape, comprehending the advantages of trusted cloud solutions ends up being imperative for companies aiming to strengthen their information security approaches. Trusted cloud solutions provide countless advantages that can enhance information security procedures.
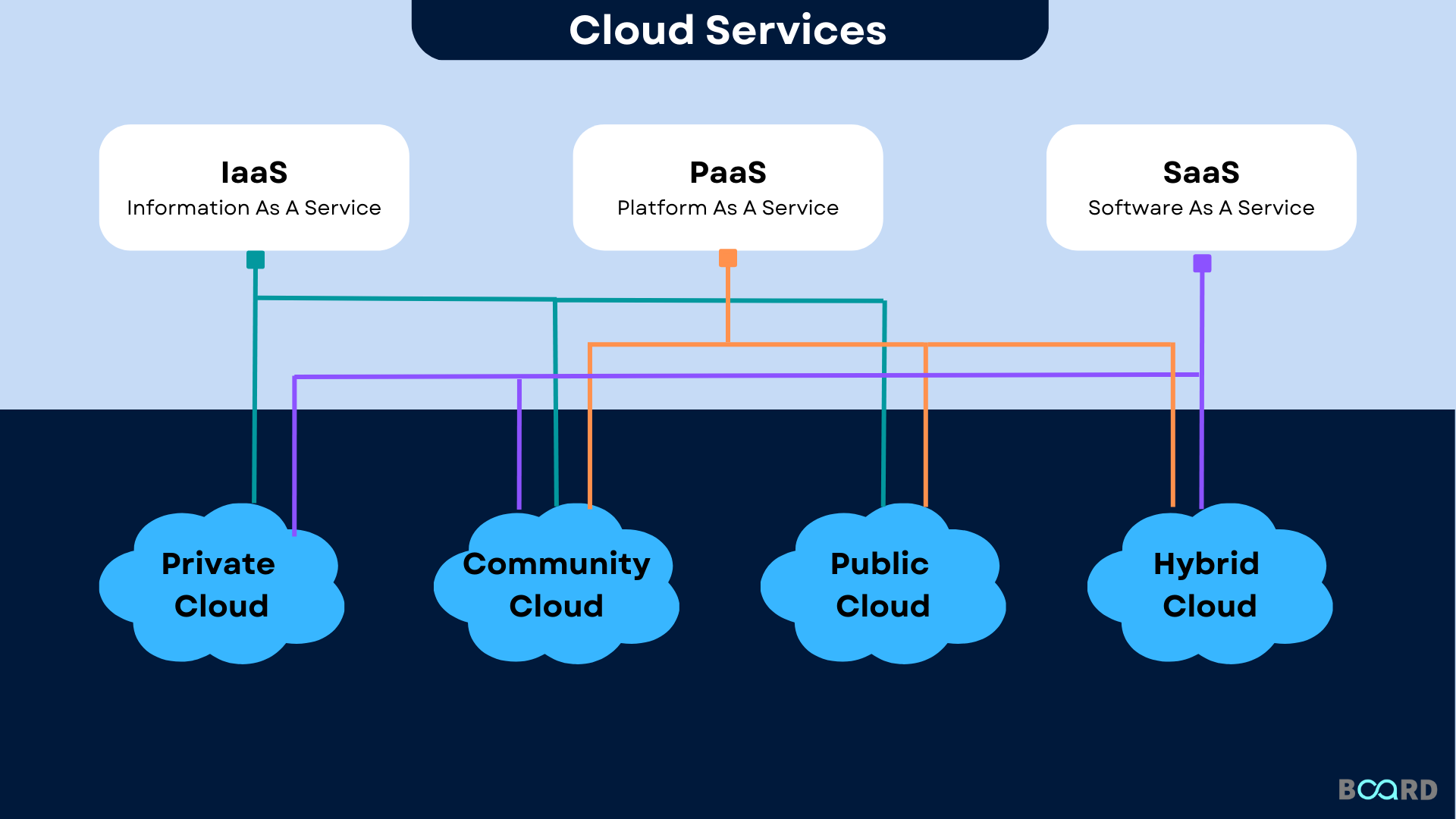
Furthermore, trusted cloud solutions give reliable backup and disaster recovery remedies, making certain information accessibility even in the occasion of unanticipated occurrences. This dependability is important for preserving business connection and lessening information loss. In general, the benefits of relied on cloud services contribute considerably to strengthening data safety and security techniques within organizations.
Secret Functions of Secure Cloud Solutions
Executing durable safety and security procedures is necessary in guaranteeing the integrity of data kept and transmitted through cloud services. In addition, safe cloud solutions offer multi-factor authentication, requiring users to supply numerous types of verification before accessing the information. These features jointly add to a more protected cloud environment, instilling confidence in individuals concerning the defense of their data.
Finest Practices for Information Security
To strengthen information safety and security in cloud environments, adhering to finest practices for data security is extremely important. File encryption plays an important role in securing delicate details kept in the cloud. Carrying out security devices, both at remainder and in transportation, makes sure that data is muddled to unauthorized users even if it is obstructed. Access control is an additional essential technique for data security. By imposing rigorous gain access to controls, companies can limit who can watch, modify, or remove information, reducing the risk of unapproved access. Regularly backing up data is also an essential facet of information protection. In case of data loss or a security violation, having updated backups allows quick healing without jeopardizing useful information. Furthermore, monitoring and bookkeeping data access and use assistance in detecting any questionable activities immediately. By following these ideal methods for data security, organizations can boost their information security stance in the cloud atmosphere.
Selecting a Trusted Cloud Supplier
Selecting a dependable cloud company is a vital decision for companies seeking to boost their information security actions. When selecting a cloud company, numerous key aspects must be taken cloud services press release into consideration to make certain dependability. First of all, organizations need to assess the service provider's protection procedures, consisting of data encryption, access controls, and conformity accreditations. A trustworthy cloud provider must have durable security protocols in position to secure information against unapproved gain access to and cyber risks.
Additionally, organizations must review the company's uptime and reliability performance history. Downtime can have significant ramifications for business operations and data access, so choosing a service provider with a tried and tested performance history of high uptime is necessary. Furthermore, organizations should consider the scalability and adaptability used by the cloud provider to fit future development and transforming business needs.
Finally, reviewing the company's consumer assistance solutions is crucial. In the event of any problems or safety violations, experienced and responsive customer assistance can make a substantial distinction in mitigating dangers and guaranteeing prompt resolutions. By carefully considering these variables, companies can choose a dependable cloud service provider that fulfills their information safety needs effectively.
Verdict
In final thought, leveraging trusted cloud solutions is important for enhancing information safety in today's digital landscape. By applying robust security procedures, advanced threat discovery abilities, and reliable back-up services, companies can efficiently safeguard beneficial info and mitigate dangers of information breaches. Picking a reputable cloud service provider and complying with ideal techniques for data defense are vital action in maintaining information integrity and making sure comprehensive security versus cyber threats.
By delegating data to trusted cloud carriers geared up with innovative security steps, services can fortify their defenses versus cyber hazards and ensure data privacy. Companies have to focus on data safety and security when embracing cloud solutions to protect against data breaches and maintain the integrity of their procedures.
Offered the climbing importance of data safety and security in the digital landscape, comprehending the advantages of relied on cloud solutions comes to be necessary for companies intending to strengthen their information defense strategies.To fortify data security in cloud environments, adhering to best practices for data security is vital. By adhering to these finest methods for data security, organizations can boost their information protection stance in the cloud setting.
Report this page